Web Application VAPT by DigiFortex
In today’s digital-first world, Web Application Security is more critical than ever. Cyber threats are constantly evolving, making it essential to test your web applications for vulnerabilities regularly. At DigiFortex, we specialize in Advanced Web Application Penetration Testing, ensuring your applications remain secure and resilient against attacks.
What is Web Application Penetration Testing?
A Web Application is a software program that runs on a web server and is accessed through a web browser. Unlike traditional software that you install on your computer, web applications operate over the internet, making them accessible from anywhere. Examples include Amazon, Flipkart, Facebook etc. Web applications typically use technologies like HTML, CSS, JavaScript, and back-end programming (e.g. Python, PHP, Java) to deliver dynamic and interactive features
Web Application Penetration Testing is a process where cybersecurity experts simulate real-world attacks on a web app to uncover security loopholes. These loopholes can include:
- Broken authentication systems
- Insecure APIs
- Cross-site scripting (XSS)
- SQL Injection
- Misconfigured security settings
At DigiFortex, we use a combination of cutting-edge tools and manual testing techniques to identify vulnerabilities that automated tools often overlook.
Request free consultation - Click Here
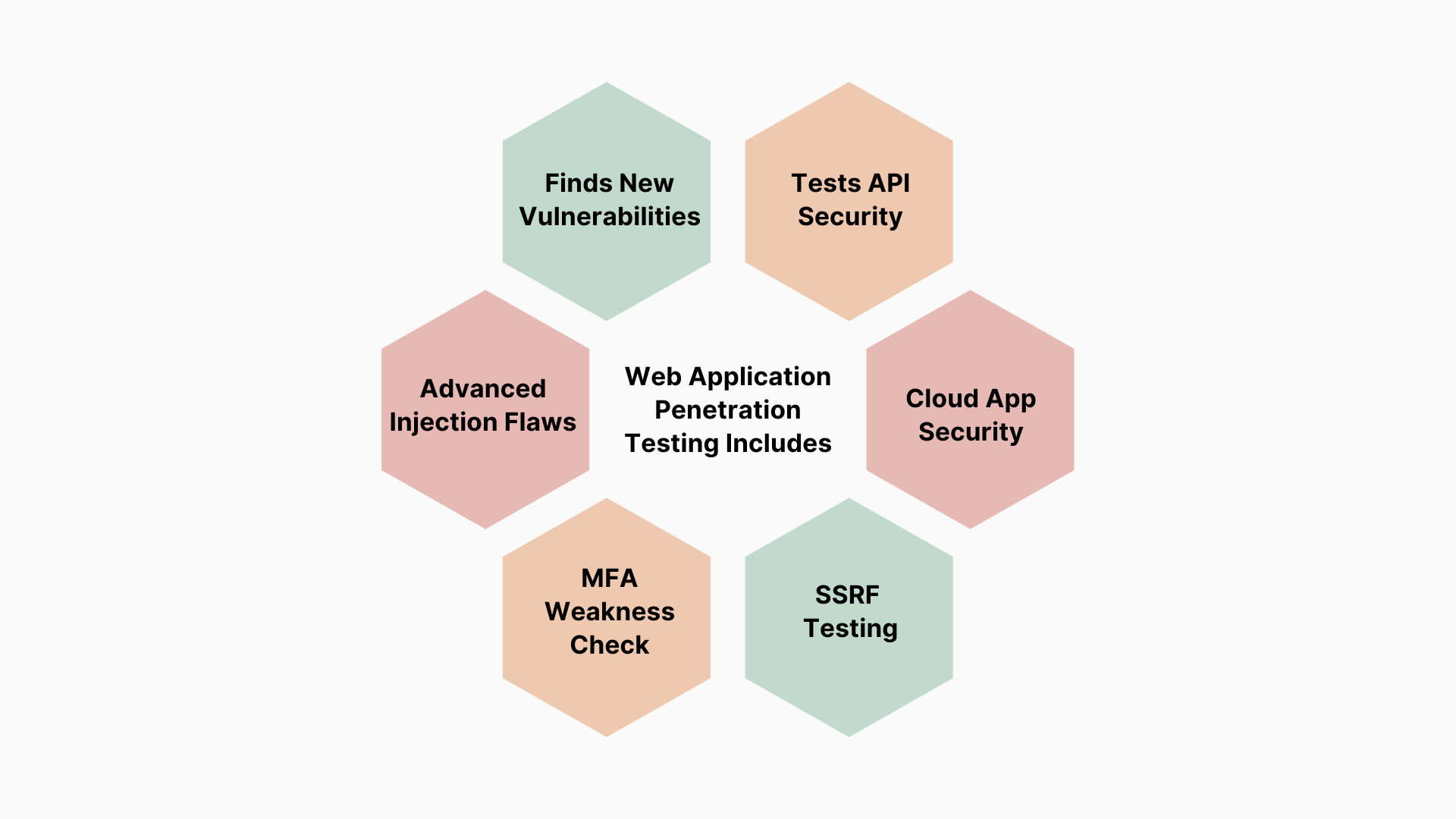
Web Application Penetration Testing Includes:
-
Finds New Vulnerabilities:
Detects previously unknown security weaknesses in web apps. -
Tests API Security:
Checks if APIs connected to the web app are secure. -
Cloud App Security:
Ensures web apps hosted on the cloud are properly configured and secure. -
SSRF Testing:
Identifies risks from attacks that misuse server functions to access internal systems. -
MFA Weakness Check:
Looks for flaws in multi-factor authentication methods. -
Advanced Injection Flaws:
Finds complex issues like script injections or data manipulation vulnerabilities.
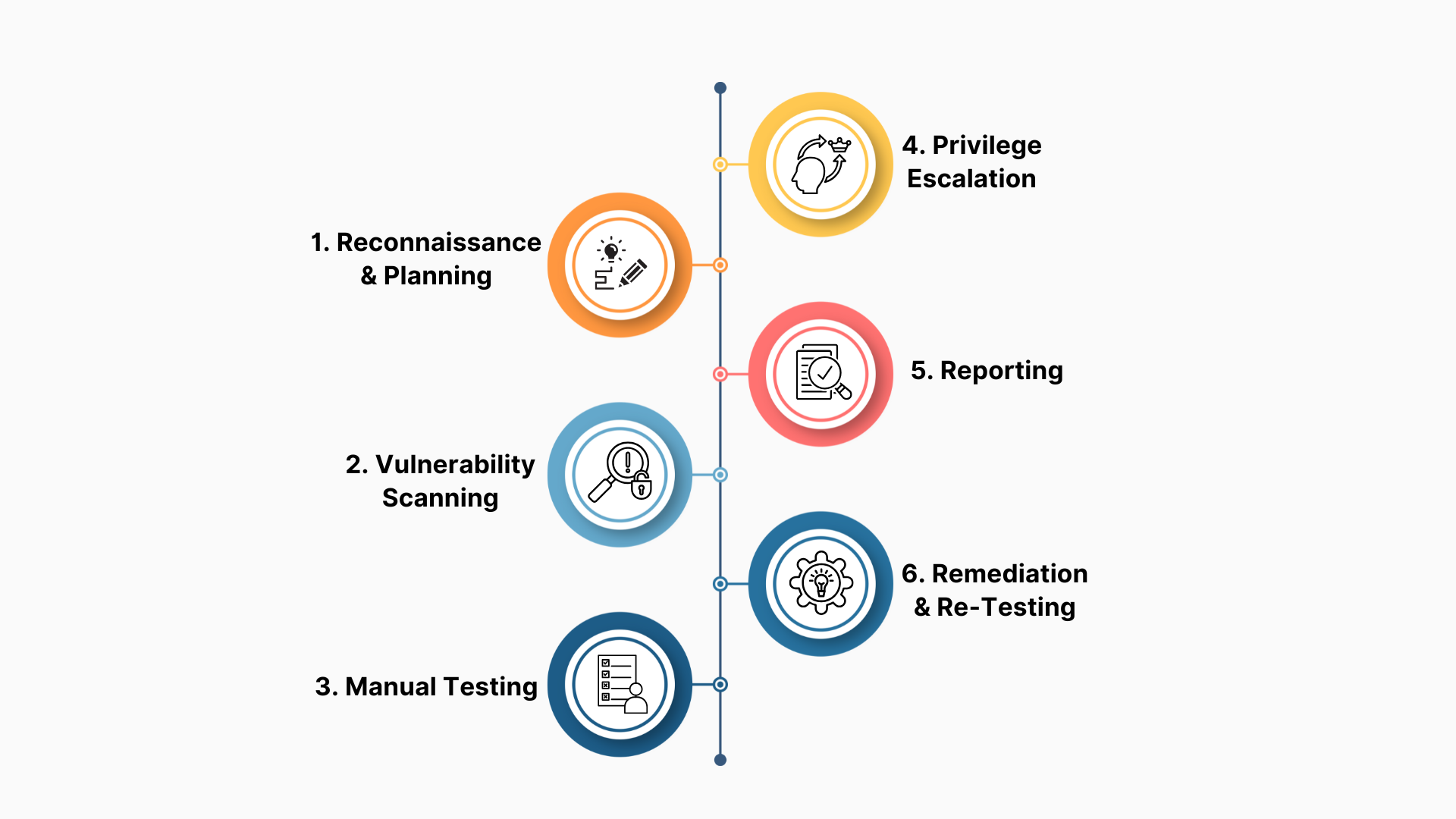
Step-by-Step Process of Web Application Penetration Testing
-
Reconnaissance and Planning
- Understand the application architecture, technologies used, and potential attack surfaces.
- Define the scope and objectives of the test.
-
Vulnerability Scanning
- Use automated tools to identify common vulnerabilities like outdated libraries, open ports, and misconfigurations.
-
Manual Testing
- Simulate attacks like SQL Injection, XSS, and authentication bypass.
- Exploit business logic vulnerabilities unique to the application’s workflows.
-
Privilege Escalation
- Test whether unauthorized users can gain elevated privileges to access sensitive data or perform restricted actions.
-
Reporting
A detailed report is prepared, highlighting vulnerabilities, exploitation methods, and remediation steps. The report typically includes:
- Executive Summary
- Technical Findings
- Risk Ratings
- Remediation Recommendations
-
Remediation and Re-Testing
- Once vulnerabilities are fixed, re-testing ensures that the issues have been resolved without introducing new ones.
Request free consultation - Click Here
Latest Trends and Techniques in Web Application Penetration Testing
-
Shift-Left Security
Integrating security testing early in the software development lifecycle (SDLC) ensures vulnerabilities are caught during the development phase. This reduces costs and enhances application security. -
DevSecOps Integration
Penetration testing tools now integrate seamlessly with DevOps pipelines, ensuring automated and continuous security testing. -
Artificial Intelligence (AI) in Penetration Testing
AI-powered tools are now used to simulate complex attack patterns and identify vulnerabilities faster. These tools can mimic sophisticated threat actors, providing a deeper analysis of an application’s weaknesses. -
Cloud-Based Penetration Testing
With the rise of cloud-hosted applications, pentesting now includes cloud-specific vulnerabilities like misconfigured S3 buckets or insecure APIs. Cloud-native testing frameworks are increasingly popular. -
Focus on API Security
As APIs are integral to modern web applications, pentesting now prioritizes API endpoints to detect issues like improper authentication, insecure data transmission, and rate-limiting flaws. -
Zero Trust Security Validation
Penetration testing now incorporates Zero Trust principles, ensuring that even internal users or systems cannot access sensitive data without explicit verification. -
Advanced Social Engineering Scenarios
Web app pentesting now includes scenarios involving phishing, credential stuffing, and session hijacking to simulate real-world attacks.
Common Vulnerabilities Found in Web Applications
-
SQL Injection
Malicious SQL code is injected to manipulate databases and extract sensitive information. -
Cross-Site Scripting (XSS)
Attackers inject malicious scripts into web pages viewed by other users. -
Cross-Site Request Forgery (CSRF)
Exploits user authentication by tricking the user into performing unintended actions on a web application. -
Insecure Deserialization
Allows attackers to execute malicious code by tampering with serialized data. -
Broken Authentication and Session Management
Weak authentication mechanisms can lead to unauthorized access. -
Security Misconfigurations
Improperly configured servers, frameworks, or security settings expose vulnerabilities. -
API Vulnerabilities
Unsecured APIs are a major concern due to improper authentication, insecure data exposure, and lack of rate limiting.
Best Practices for Effective Web Application Penetration Testing
-
Use OWASP Top 10 as a Baseline
Focus on the vulnerabilities listed in the OWASP Top 10, which include the most critical web application risks. -
Incorporate DevSecOps Practices
Integrate security testing into the development lifecycle to identify and fix vulnerabilities early. -
Leverage Modern Penetration Testing Tools
Use advanced tools and platforms that offer automated scanning, AI-driven analysis, and cloud-specific testing. -
Conduct Regular Testing
Perform Penetration Testing periodically, especially after major updates or new feature releases. -
Engage Certified Experts
Hire professionals with certifications like CEH, CISSP, or OSCP for thorough and reliable testing. -
6. Document Everything
Keep detailed records of vulnerabilities, remediation efforts, and testing methodologies for future reference.
Request free consultation - Click Here
How DigiFortex Stands Out
-
Certified Experts
CIPPE, CCSA, CCNA, HPOV, DCPLA, CEH, CISSP, CISM, ISO27001 LA. -
ISO 27001:2022 certified and CERT-In empanelled
DigiFortex is ISO 27001:2022 certified and CERT-In empanelled for providing Information security services. We bring unparalleled expertise to every project. -
Proven Methodologies
Our solutions align with industry best practices like OWASP, SANA, CERT, NIST, ISO, SOC 2 ensuring your applications are secure and compliant. -
Cutting-Edge Tools
We leverage the latest technologies for vulnerability scanning, threat detection, and risk management. -
Comprehensive Reporting
Detailed yet simple reports with actionable insights to fix vulnerabilities quickly. -
6. Continuous Support
Beyond testing, we guide your team in strengthening web application defences.
Benefits of Choosing DigiFortex
- Enhanced web application security
- Protection against zero-day vulnerabilities
- Improved customer trust
- Seamless compliance with industry standards
Why Wait? Secure Your Web Applications Today!
Your web applications are gateways to your business. Ensure they are secure with DigiFortex’s Web Application Penetration Testing Services. Contact us now to schedule a consultation and take the first step toward a cyber-secure future.
At DigiFortex, your security is our priority. Let’s protect your business together!
Request free consultation - Click Here
Let’s Build a Stronger Future Together
Your security is our mission. Contact Digifortex today! to learn how our Web Application Penetration Testing Services can help you stay ahead of cyber threats and build a future of confidence and resilience.