Software Composition Analysis by DigiFortex
In today’s fast-paced digital world, software development is evolving rapidly. Developers now rely heavily on open-source components to speed up the development process, reduce costs, and focus on innovative features. While this is great for agility, it brings a major concern: how do we ensure these components are secure, reliable, and compliant with licensing requirements? This is where Software Composition Analysis (SCA) comes in.
SCA is a technology-driven approach to analyse and manage open-source components in your software applications. It helps organizations identify vulnerabilities, license risks, and outdated components in their codebase.
At DigiFortex, we believe the solution lies in Software Composition Analysis (SCA)—a powerful approach to safeguard your software ecosystem while staying ahead of threats.
Request free consultation - Click Here
What is Software Composition Analysis?
SCA is the process of examining the open-source components, libraries, and dependencies within a software application.
Open-source components are reusable software building blocks with publicly available code that anyone can use, modify, and share. They save time for developers by providing ready-made solutions for common tasks.
Software composition analysis helps developers safely use open-source packages by identifying and managing security risks, legal issues, and compliance concerns.
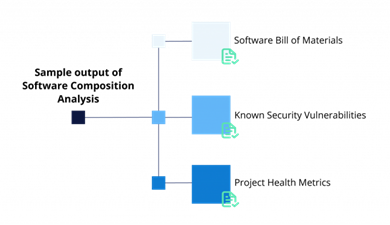
Software Composition Analysis (SCA) provides essential features like:
- Software Bill of Materials (SBOM): A detailed list of all open-source components and dependencies used in a project.
- Known Security Vulnerabilities: Identification of any security issues in the open-source components.
- Project Health Metrics: Insights into the quality, maintenance, and overall reliability of the open-source projects being used.
Why is SCA Important?
Software Composition Analysis (SCA) is crucial in modern software development for several reasons:
-
Open-Source Usage is Growing
- Over 90% of modern applications use open-source components.
- SCA helps developers manage these components safely and efficiently.
-
Increase in Cyber Threats
- Cybercriminals often exploit vulnerabilities in widely used libraries. For instance, the infamous Log4Shell vulnerability in Log4j, a popular Java library, caused a global security crisis in 2021. Without SCA, such risks might go unnoticed.
-
Ensures Legal Compliance
- Open-source licenses come with specific rules.
- SCA ensures you follow license requirements, avoiding legal troubles.
-
Improves Software Quality
- SCA tools track project health metrics, like updates and community activity.
- This ensures you're using reliable and actively maintained components.
-
Speeds Up Development
- By automating security checks, SCA reduces manual work for developers.
- This leads to faster, more secure software delivery.
-
Aligns with DevSecOps
- SCA integrates into modern DevSecOps pipelines, enabling early detection of issues.
- It supports shifting security left, saving time and resources.
What Are the Risks of Using Open-Source Components?
Open-source software (OSS) has revolutionized the tech industry, but it comes with its own set of risks:
-
Security Vulnerabilities
OSS is publicly available, which means anyone, including attackers, can review its code. If vulnerabilities exist, they can be exploited by malicious actors. Examples include the Heartbleed bug in OpenSSL and the Log4Shell vulnerability. -
Outdated or Unmaintained Components
Some open-source libraries become outdated or abandoned by their maintainers. Using such components can lead to compatibility issues or leave applications exposed to vulnerabilities that are no longer being patched. -
License Compliance Risks
Each open-source component is governed by a license, such as MIT, GPL, or Apache. Misusing these licenses—whether intentionally or unintentionally—can result in legal consequences or force organizations to open-source their proprietary code. -
Dependency Risks
Modern applications often rely on indirect or transitive dependencies. A single vulnerable dependency deep within the chain can compromise the entire application. -
Operational Risks
Relying heavily on open-source components without understanding their limitations can lead to operational challenges, such as performance bottlenecks or integration issues.
Latest Trends in SCA Technology
-
AI-Driven Insights
SCA tools are now using AI to predict which vulnerabilities are likely to be exploited, helping prioritize remediation efforts. -
Real-Time Monitoring
Modern tools provide real-time alerts for vulnerabilities discovered after deployment, ensuring continuous protection. -
Integration with DevSecOps
SCA is becoming an integral part of DevSecOps, enabling seamless security checks throughout the development lifecycle. -
Focus on SBOMs (Software Bill of Materials)
The adoption of SBOMs is growing as organizations strive for greater transparency and accountability in their software supply chains.
How SCA Works at DigiFortex
Open-source software (OSS) has revolutionized the tech industry, but it comes with its own set of risks:
-
Discovery and Inventory
We scan your codebase to identify all open-source and third-party components, including their dependencies. -
Vulnerability Assessment
Our tools cross-check components against global vulnerability databases, such as CVE and NVD, to detect known security flaws. -
License Compliance Review
We analyse the licensing terms of each component to ensure your usage aligns with legal and regulatory standards. -
Detailed Risk Reporting
We provide comprehensive reports highlighting vulnerabilities, risks, and actionable recommendations. -
Continuous Monitoring
Even after deployment, we monitor your software for new vulnerabilities and compliance changes, keeping your systems up-to-date and secure.
Request free consultation - Click Here
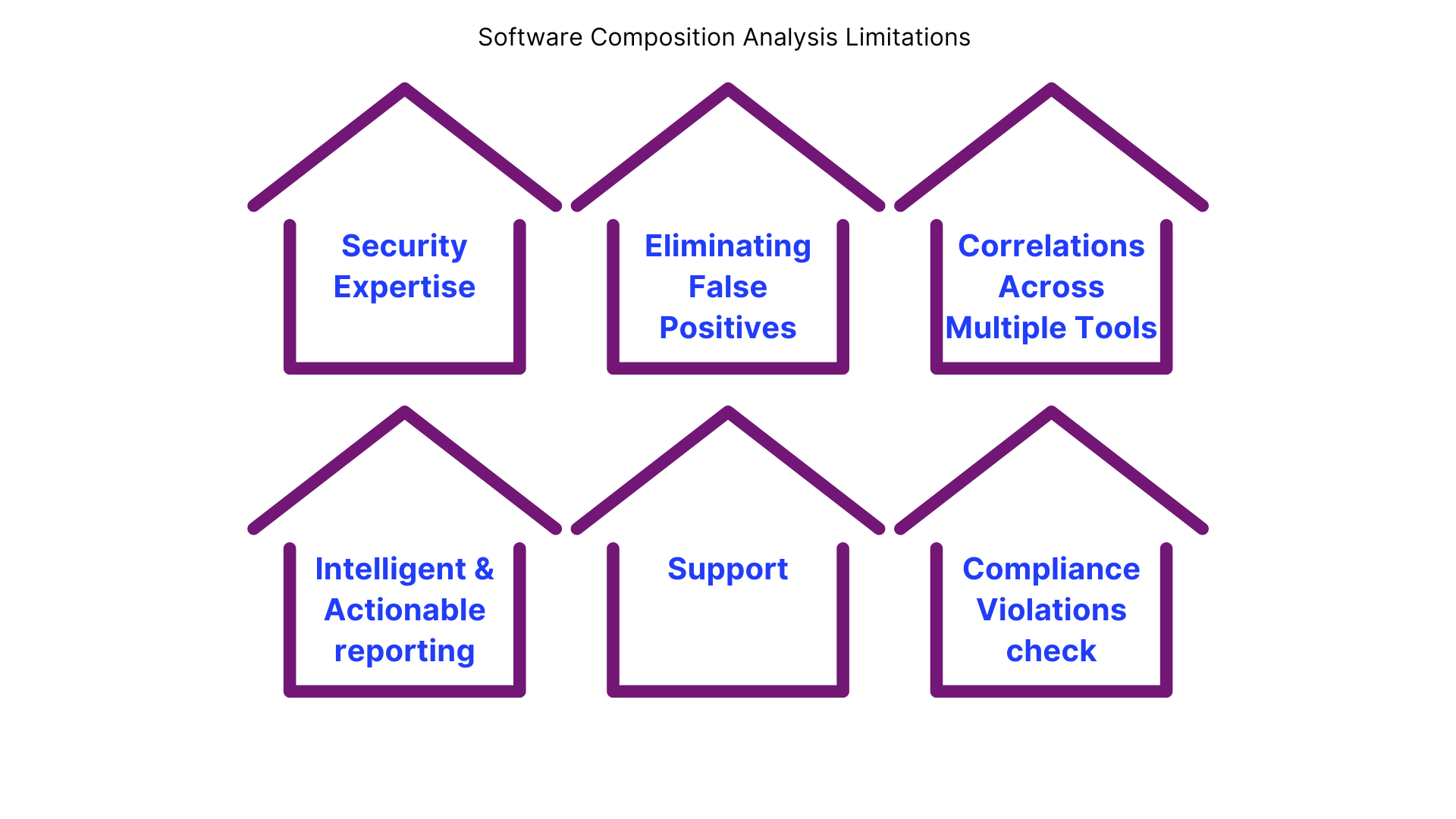
limitations of Software Composition Analysis (SCA):
-
Security Expertise Required
SCA tools may need expert knowledge to interpret the results correctly. A basic user might struggle to fully understand or fix complex security issues. -
Eliminating False Positives
SCA tools might flag issues that aren’t actually problems (false positives), which can waste time and resources. Reducing these requires fine-tuning and experience. -
Correlations Across Multiple Tools
SCA tools might not always work well with other security tools, making it hard to get a complete view of your system’s security from multiple sources. -
Intelligent & Actionable Reporting
Not all SCA tools provide clear, easy-to-understand reports that tell you exactly what actions to take. Sometimes, the reports are too technical or vague for easy decision-making. -
Support
Some SCA tools may lack sufficient customer support or resources, making it difficult to resolve issues when they arise. -
Compliance Violations Check
While SCA helps with security, it might not catch all compliance issues, such as license violations or regulatory requirements, depending on the tool and setup.
Why Choose DigiFortex for SCA?
-
Top Security Expertise
DigiFortex brings in-depth security knowledge and experience to ensure your software is protected from vulnerabilities. -
Unlimited SCA Scans with Multiple Tools
We offer unlimited scans using a variety of top-tier tools, providing comprehensive security checks for your open-source components. -
Eliminating False Positives
Our advanced approach minimizes false positives, ensuring that your security team focuses on real threats, not non-issues. -
Correlations Across Multiple Tools
We integrate data from multiple security tools, giving you a clearer, more accurate view of your project’s security posture. -
Continuous Monitoring
DigiFortex provides ongoing monitoring to keep track of vulnerabilities and threats, ensuring you're always protected. -
Intelligent & Actionable Reporting
Our reports are clear, insightful, and actionable, helping you take immediate steps to secure your software. -
Unlimited Support
Our team is always available to support you, providing quick resolutions and guidance whenever you need it. -
Policy Violations Monitoring
We actively monitor your projects for any policy violations, helping you stay compliant with internal and external standards. -
Compliance Violation Check
DigiFortex ensures your software complies with regulations, preventing legal and regulatory issues down the road. -
License Violations Check
We check for potential license violations in open-source components, ensuring you stay on the right side of legal requirements.DigiFortex SCA gives you peace of mind, knowing your open-source software is secure, compliant, and well-maintained.
What Makes DigiFortex’s Approach to SCA Unique?
At DigiFortex, we go beyond traditional SCA tools to deliver comprehensive protection and compliance. Here’s what sets us apart:
-
Tailored Risk Management
We customize our SCA solutions to fit your business needs. Whether you’re a startup or an enterprise, our approach aligns with your software development lifecycle (SDLC) and compliance requirements. -
Proactive Vulnerability Mitigation
Our cutting-edge tools and expert analysts detect and address vulnerabilities early in the development process, preventing costly fixes later. -
AI-Driven Insights
We leverage AI-powered analytics to predict emerging risks, prioritize fixes, and optimize your software’s security posture. -
Seamless Integration
DigiFortex’s SCA integrates smoothly into your existing DevSecOps pipelines, ensuring continuous monitoring without disrupting workflows. -
Focus on Business Continuity
We don’t just scan for issues; we ensure your software remains operational and reliable. Our solutions minimize downtime while enhancing security and compliance.
Request free consultation - Click Here
Software Composition Analysising Services by DigiFortex: Proactively Securing Your Business
In today’s digital era, cyber threats are not just a possibility—they are a reality. Businesses of all sizes face risks that can disrupt operations, harm reputations, and compromise sensitive data. At DigiFortex, we go beyond traditional cybersecurity to offer Software Composition Analysising Services—a proactive and strategic approach to testing your defences against real-world cyberattacks.
We don’t just uncover vulnerabilities; we help you strengthen your security posture and build confidence in your digital resilience.
Request free consultation - Click Here
Let’s Build a Stronger Future Together
Your security is our mission. Contact Digifortex today! to learn how our Software Composition Analysising Services can help you stay ahead of cyber threats and build a future of confidence and resilience.
