IoT Penetration Testing: Building a Secure Future for Connected Devices
The Internet of Things (IoT) has transformed industries, homes, and businesses by seamlessly connecting devices to the digital world. From smart appliances to industrial sensors, IoT devices play a vital role in driving innovation. However, as IoT ecosystems grow, so does their vulnerability to cyber threats. Protecting these devices is no longer optional—it’s critical.
At DigiFortex, we provide cutting-edge IoT penetration testing services to safeguard your connected devices and networks. In this blog, we’ll explore the significance of IoT penetration testing, how it works, and why it’s essential for your business's cybersecurity strategy.
The Growing Importance of IoT Security
The IoT ecosystem is expanding rapidly, with billions of devices now connected worldwide. While this interconnectivity drives efficiency and convenience, it also creates a vast attack surface for cybercriminals.
Key IoT Security Concerns:
- Data Breaches: Compromised IoT devices can expose sensitive personal or corporate data.
- DDoS Attacks: IoT devices can be hijacked to form botnets, causing widespread service disruption.
- Industrial Espionage: In sectors like manufacturing and healthcare, IoT vulnerabilities can lead to intellectual property theft or operational sabotage.
- Compliance Risks: Regulations such as GDPR, HIPAA, and CCPA mandate the protection of data, with non-compliance resulting in heavy fines.
IoT penetration testing helps organizations uncover these risks before they become real-world problems, ensuring both operational continuity and regulatory compliance.
What Is IoT Penetration Testing?
IoT (Internet of Things) is a network of smart devices connected to the internet, enabling them to communicate and share data. These devices can include things like smart home gadgets (e.g., smart lights, thermostats), wearable devices (e.g., fitness trackers), industrial sensors, and even connected cars
The goal of IoT is to make life easier and more efficient by automating tasks, collecting data, and enabling remote control of devices.
IoT penetration testing involves simulating cyberattacks to identify vulnerabilities in IoT devices, their communication protocols, and the networks they connect to. Unlike traditional IT systems, IoT ecosystems consist of a diverse mix of hardware, firmware, software, and cloud-based components.
Key Goals of IoT Penetration Testing:
- Identify Weaknesses: Detect vulnerabilities in devices, networks, and cloud integrations.
- Assess Exploitable Risks: Determine how attackers could misuse a device or compromise an entire system.
- Strengthen Security: Provide actionable recommendations to enhance the security of IoT deployments.
IoT Penetration Testing Includes:
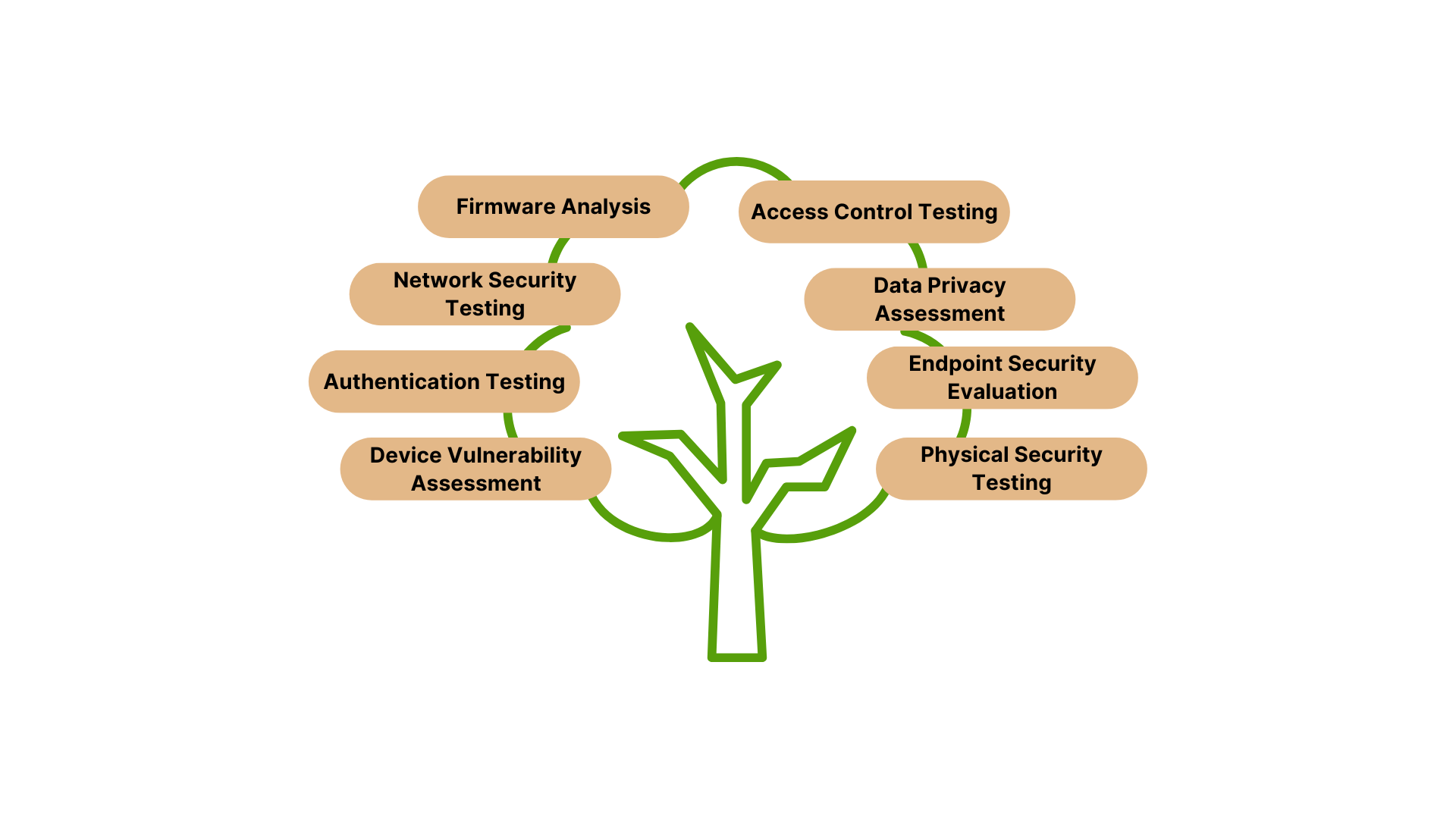
- Device Vulnerability Assessment: Identifies security flaws in IoT devices, firmware, and hardware.
- Authentication Testing: Checks for weak or default credentials and insecure authentication mechanisms.
- Network Security Testing: Evaluates communication protocols and encryption used for data transmission.
- Firmware Analysis: Tests for vulnerabilities like hardcoded keys, backdoors, and insecure updates.
- Access Control Testing: Verifies restrictions on unauthorized access to IoT devices and their ecosystems.
- Data Privacy Assessment: Ensures sensitive data collected or transmitted by devices is protected.
- Endpoint Security Evaluation: Assesses integration points between IoT devices and broader networks for potential exploits.
- Physical Security Testing: Identifies risks from physical tampering or device theft.
The DigiFortex Approach to IoT Penetration Testing
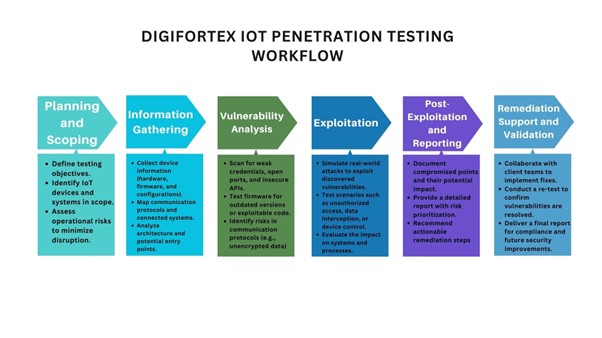
At DigiFortex, we follow a structured, tailored approach to IoT penetration testing to ensure comprehensive security assessments. Here’s how our process works:
-
Planning and Scoping:
- Collaborate with clients to define testing objectives and identify critical IoT components.
- Assess potential risks to ensure minimal disruption during the testing process.
-
Information Gathering:
- Collect data on IoT device configurations, firmware versions, communication protocols, and network architecture.
- Analyze the ecosystem for potential entry points and weak links.
-
Vulnerability Analysis:
- Perform in-depth scans using specialized tools to identify vulnerabilities such as:
- Default credentials
- Unpatched firmware
- Insecure APIs
- Weak encryption mechanisms
-
Exploitation:
- Simulate real-world attacks to test the exploitability of discovered vulnerabilities.
- Assess the potential impact on devices, networks, and data integrity.
-
Post-Exploitation and Reporting:
- Evaluate the extent of compromise and its implications.
- Provide a detailed report with findings, risk levels, and step-by-step remediation strategies.
-
Remediation Support and Validation:
- Work closely with your team to implement recommended fixes.
- Conduct a re-test to ensure all vulnerabilities are adequately addressed.
- Ongoing Monitoring: Continuously monitor the target environment for new vulnerabilities and threats.
Common IoT Vulnerabilities Uncovered During Penetration Testing
IoT penetration testing often reveals these prevalent security issues:
- Default or Weak Credentials: Many IoT devices ship with default passwords, making them easy targets for attackers.
- Insecure Communication Protocols: Lack of encryption in data transmission leaves devices vulnerable to interception.
- Outdated Firmware: Unpatched devices remain susceptible to known exploits.
- Inadequate Access Controls: Poor user authentication mechanisms allow unauthorized access.
- Lack of Data Privacy Measures: Sensitive information is often stored or transmitted without sufficient protection.
The Benefits of IoT Penetration Testing
Investing in IoT penetration testing provides numerous advantages:
- Proactive Risk Mitigation: Identify and address vulnerabilities before they are exploited, minimizing downtime and potential losses.
- Compliance with Regulations: Ensure adherence to industry standards and legal requirements, such as GDPR and HIPAA, to avoid penalties.
- Enhanced Trust and Reputation: Demonstrate a commitment to protecting customer data and maintaining system integrity.
- Strengthened Resilience: Build robust IoT systems that can withstand advanced cyberattacks.
- Competitive Advantage: A secure IoT deployment positions your organization as a trusted leader in your industry.
Challenges in IoT Penetration Testing
IoT penetration testing is not without its complexities. Key challenges include:
- Diverse Device Ecosystems: IoT environments consist of a wide range of devices with varying configurations.
- Limited Device Resources: Many IoT devices have constrained processing power, making traditional security measures unsuitable.
- Real-time Impact: Testing live environments may disrupt critical operations if not carefully managed.
- Proprietary Protocols: IoT devices often use custom protocols, requiring specialized expertise to analyze.
At DigiFortex, our team of experts is equipped to tackle these challenges, ensuring thorough and effective assessments tailored to your IoT environment.
IoT Penetration Testing: Advanced Techniques and Considerations
- AI-Powered Testing: Leverage artificial intelligence (AI) and machine learning (ML) algorithms to automate vulnerability identification, analyze threat intelligence, and improve the efficiency and effectiveness of penetration testing.
- IoT-Specific Testing Tools: Utilize specialized tools designed for testing IoT devices, such as those that can analyse firmware, identify unique vulnerabilities, and simulate real-world attack scenarios.
- Cloud-Based Testing: Conduct penetration testing in cloud environments to evaluate the security of cloud-based IoT deployments and identify vulnerabilities specific to cloud infrastructure.
- 5G and Edge Computing Considerations: Evaluate the security implications of 5G networks and edge computing on IoT deployments, including potential attack vectors and mitigation strategies.
- Privacy and Ethical Considerations: Ensure that penetration testing activities are conducted in a responsible and ethical manner, respecting user privacy and data protection regulations.
Best Practices for IoT Security
In addition to penetration testing, these best practices can help enhance IoT security:
- Strong Authentication: Use unique, complex passwords and multi-factor authentication for all IoT devices.
- Regular Firmware Updates: Keep devices up to date with the latest security patches.
- Encrypt Communication: Use strong encryption protocols like TLS for data transmission.
- Network Segmentation: Isolate IoT devices from critical systems to limit the impact of potential breaches.
- Continuous Monitoring: Implement real-time monitoring to detect and respond to anomalies promptly.
Why Choose DigiFortex for IoT Penetration Testing?
At DigiFortex, we understand that IoT security requires a specialized approach. Here’s what sets us apart:
- Certified Experts: CIPPE, CCSA, CCNA, HPOV, DCPLA, CEH, CISSP, CISM, ISO27001 LA.
- ISO 27001:2022 certified and CERT-In empanelled: DigiFortex is ISO 27001:2022 certified and CERT-In empanelled for providing Information security services. We bring unparalleled expertise to every project.
- Industry Expertise: Our team has extensive experience in securing IoT ecosystems across various industries.
- Tailored Solutions: We customize our testing methodologies to suit your specific needs.
- Comprehensive Reporting: Our actionable insights help you prioritize and address vulnerabilities effectively.
- End-to-End Support: From initial assessment to remediation, we’re with you every step of the way.
Conclusion
The rise of IoT has brought immense opportunities—and unprecedented risks. IoT penetration testing is your first line of defense against cyber threats, ensuring the security and reliability of your connected devices and networks.
At DigiFortex, we’re committed to helping organizations like yours stay ahead of evolving cyber threats. By partnering with us, you can confidently embrace the future of IoT, knowing your systems are secure.
Secure your IoT ecosystem today with DigiFortex. Contact Digifortex today! to learn more about our IoT penetration testing services.