Mobile Application VAPT by DigiFortex
In today's digital age, mobile applications are a vital part of our daily lives. From banking apps to social media platforms, mobile devices store and transmit a wide range of sensitive information. As mobile apps become more integrated into our business and personal activities, the risks associated with their security increase. Mobile apps can be vulnerable to cyberattacks, and this is where Mobile Penetration Testing comes into play. At DigiFortex, we specialize in mobile penetration testing to ensure that your mobile applications are secure, protecting your business and users from data breaches and cyber threats.
What Is Mobile Penetration Testing?
Mobile Penetration Testing is a simulated attack on a mobile application to uncover security vulnerabilities before malicious actors exploit them. It involves analysing an app's source code, architecture, and backend infrastructure to identify potential weaknesses.
Mobile penetration testing covers:
- iOS Applications
- Android Applications
- Hybrid Applications (React Native, Flutter, etc.)
- APIs and Backend Servers
Request free consultation - Click Here
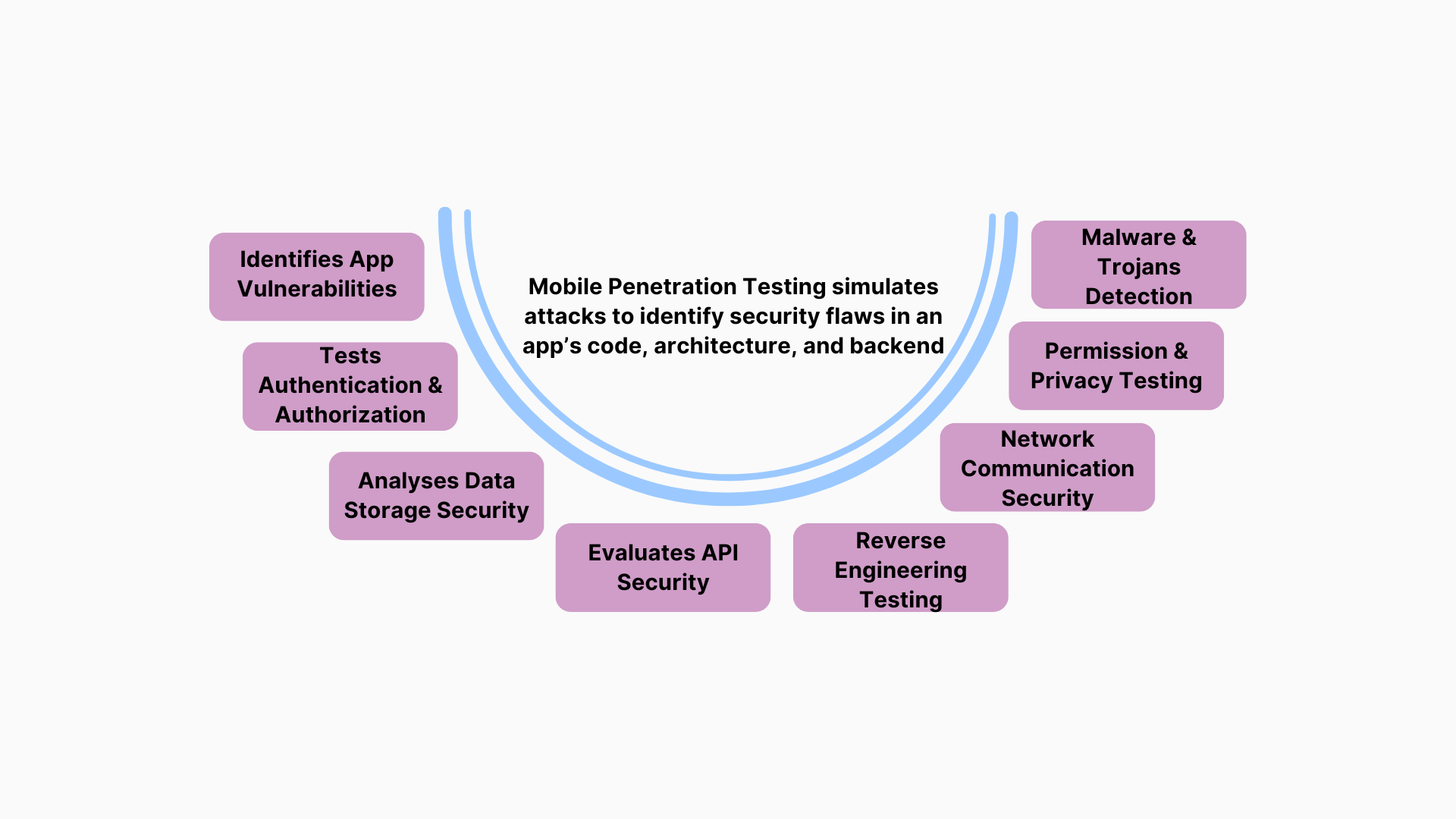
Mobile Application Penetration Testing in VAPT Includes:
-
Identifies App Vulnerabilities:
Detects security flaws like insecure storage, code injection, and XSS. -
Tests Authentication & Authorization:
Ensures secure login, session management, and role-based access. -
Analyses Data Storage Security:
Checks for improper storage of sensitive data in local databases, logs, or cache. -
Evaluates API Security:
Assesses communication between the mobile app and backend servers for weaknesses. -
Reverse Engineering Testing:
Identifies risks of code tampering, recompilation, or repackaging attacks. -
Network Communication Security:
Ensures secure transmission of data using encryption and HTTPS. -
Permission & Privacy Testing:
Identifies risks of code tampering, recompilation, or repackaging attacks. -
Malware & Trojans Detection:
Scans for potential security risks from third-party integrations or SDKs.
Importance of Mobile App Penetration Testing:
-
Identify and Fix Vulnerabilities
Mobile penetration testing helps organizations uncover weaknesses in their apps, enabling them to fix vulnerabilities before attackers exploit them. -
Protect User Data & Maintain Trust
With sensitive user information at stake, securing mobile applications protects user privacy and builds trust in the app. -
Compliance
Regulations such as GDPR, HIPAA, and PCI DSS mandate regular testing to ensure app security and compliance. -
Platform-Specific Risks
Each platform (iOS and Android) has unique security challenges, making thorough testing essential to address platform-specific vulnerabilities. -
Secure API Integration
APIs are often the backbone of mobile apps. Penetration testing ensures that APIs are secure and free from issues such as excessive data exposure or broken authentication.
Common Vulnerabilities in Mobile Apps:
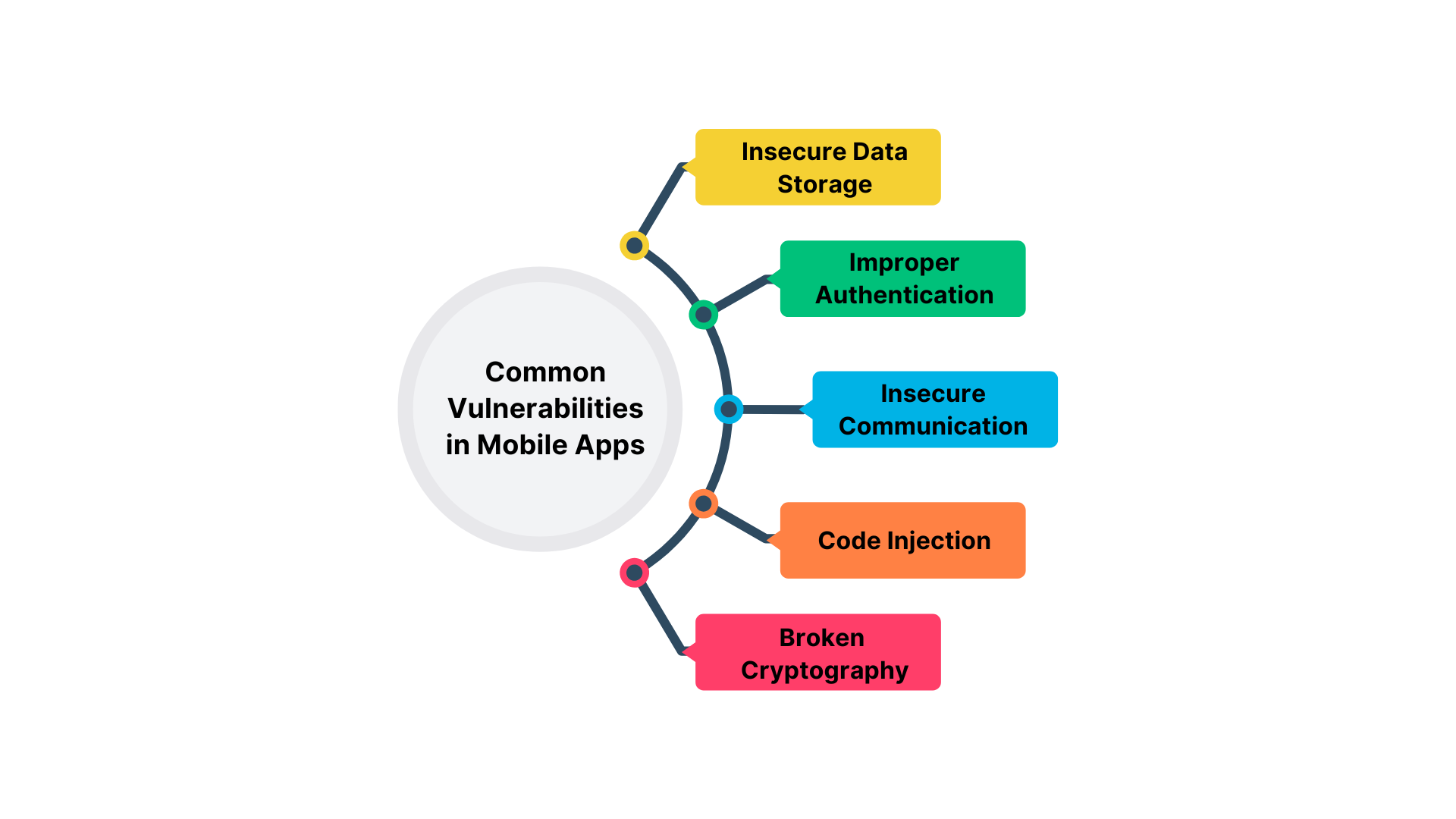
Penetration testers identify common security flaws in mobile applications, such as:
-
Insecure Data Storage:
Storing sensitive data on the device or in the cloud without proper encryption. -
Improper Authentication:
Weak or broken authentication mechanisms, such as a lack of multi-factor authentication or improper password storage. -
Insecure Communication:
Transmitting sensitive data over unencrypted channels, making it vulnerable to eavesdropping. -
Code Injection:
Flaws that allow attackers to inject malicious code into mobile applications, such as SQL injection or command injection. -
Broken Cryptography:
Use of outdated or weak encryption algorithms that attackers can easily break.
Request free consultation - Click Here
Latest Trends in Mobile Penetration Testing:
-
Testing Super Apps
Super apps, which offer multiple services within one platform, have a significantly larger attack surface. Each module is tested independently for vulnerabilities. -
IoT Integration Testing
Many mobile apps integrate with IoT devices like wearables and smart appliances. We test communication protocols (e.g., MQTT, CoAP) and device authentication. -
Continuous Testing in DevOps
We integrate penetration testing into CI/CD pipelines for real-time detection and remediation of vulnerabilities during development. -
Enhanced Privacy Testing
Focus on data privacy compliance by identifying issues like unnecessary permissions, location tracking, and unauthorized data collection.
DigiFortex Mobile Penetration Testing Methodology:
At DigiFortex, We follow a structured and advanced approach to mobile penetration testing:
-
Preparation & Discovery
We begin by gathering essential information about the app:
- Static Application Security Testing (SAST): We analyse the app’s source code for vulnerabilities such as hardcoded credentials, insecure storage, and sensitive data leaks using tools like MobSF and SonarQube.
- Public Information Gathering: We collect publicly available data to spot any potential security risks.
- Traffic Analysis: We monitor the app’s data transfer for weaknesses like weak encryption or unsecured communication.
-
Assessment & Analysis
In this phase, we dive deeper to identify potential vulnerabilities:
- Dynamic Application Security Testing (DAST): We simulate real-world attacks on the app during runtime to uncover issues like insecure data transmission, session management flaws, and improper error handling using tools like Burp Suite and OWASP ZAP.
- API Security Testing: We assess backend APIs for common vulnerabilities such as broken authentication, excessive data exposure, and insecure endpoints with tools like Postman and Insomnia
- Code & Runtime Analysis: We scan the app’s code and test its runtime behavior to identify vulnerabilities like SQL injections, cross-site scripting (XSS), and other runtime flaws.
- Architecture Review: We analyze the app's architecture to identify weaknesses in the system, including backend configurations and data storage practices.
- Reverse Engineering: We decompile the app to examine its logic, uncover hardcoded secrets, and assess cryptographic implementations using tools like JADX and Apktool.
- File System Analysis: We check how the app stores data locally to prevent sensitive data exposure.
- App Interaction Review:App Interaction Review: We investigate how the app interacts with other apps and devices to identify risks of unauthorized access.
-
Platform-Specific Testing
We evaluate platform-specific vulnerabilities:
- Android: We check for vulnerabilities like exported activities, unprotected content providers, and insecure intents.
- iOS: We assess risks such as weak keychain protections, binary analysis, and insecure file storage.
-
Exploitation
We simulate real-world attacks based on identified vulnerabilities to understand how they could be exploited in practice.
-
Reporting & Remediation
After testing, we provide a detailed report with:
- Identified Vulnerabilities: Ranked based on their severity and potential impact.
- Exploitation Proofs:Showing how the vulnerabilities could be exploited.
- Remediation Recommendations: Guidance for developers to fix the issues and strengthen app security.
- Rescanning: After fixes are applied, we re-scan the app to verify the vulnerabilities have been fully addressed.
This methodology ensures that your mobile app is tested from all angles, addressing vulnerabilities that could potentially be exploited. Ready to safeguard your app?
Request free consultation - Click Here
Advanced Techniques in Mobile Penetration Testing:
-
Testing for Jailbreak/Root Detection
- Ensure that the app detects and responds to devices that have been rooted or jailbroken, as these devices are more vulnerable to attacks.
-
Assessing Code Obfuscation
- Verify that the app’s code is obfuscated to prevent reverse engineering and intellectual property theft.
- Tools like ProGuard and R8 are commonly used for Android obfuscation.
-
Analyzing Cryptographic Implementations
- Ensure that the app uses strong cryptographic algorithms and securely stores encryption keys.
- Identify weak or custom cryptographic algorithms that may compromise security.
-
Biometric Authentication Testing
- Test the security of biometric authentication mechanisms like fingerprint and facial recognition.
- Ensure fallback mechanisms are secure and do not bypass security protocols.
-
Cloud and Backend Integration Testing
- Assess the security of cloud storage and backend servers that support the app.
- Check for misconfigurations, unprotected storage buckets, and overly permissive IAM policies.
Why Choose DigiFortex for Mobile Penetration Testing?
-
Advanced Techniques
DigiFortex employs the latest methodologies to identify vulnerabilities across Android, iOS, and hybrid apps. We ensure your mobile applications are secure from all angles, including the app's code, backend APIs, and cloud integrations. -
Certified Experts
Our team includes industry-certified professionals (CISSP, CEH, OSCP) with deep expertise in mobile app security, ensuring high-quality testing and actionable results. -
Tailored Security Solutions
Every app is unique, and so are its vulnerabilities. We customize our penetration testing approach to address your app’s specific security needs and industry requirements. -
Compliance Assurance
We help businesses meet regulatory requirements like GDPR, HIPAA, PCI DSS, and ISO 27001 by providing thorough testing and compliance-focused recommendations.
Commonly used Mobile Penetration testing tools at DigiFortex:
-
Frida
Dynamic instrumentation framework. -
Burp Suite
Analyse and modify HTTP/S traffic. -
MobSF
Comprehensive mobile app security testing framework. -
Postman
API testing and validation. -
APKTool
Reverse engineering Android apps. -
IDA Pro
Advanced disassembler for binary analysis.
Request free consultation - Click Here
Partner with DigiFortex Today
Mobile penetration testing is no longer optional—it’s a necessity. With threats evolving rapidly, protecting your mobile applications requires a proactive and advanced approach. DigiFortex provides cutting-edge mobile security services designed to keep your applications secure, your users safe, and your business thriving.
Get in touch with DigiFortex today to ensure your mobile apps are resilient against cyber threats and compliant with industry standards.
Request free consultation - Click Here
Let’s Build a Stronger Future Together
Your security is our mission. Contact Digifortex today! to learn how our Mobile Application Penetration Testing Services can help you stay ahead of cyber threats and build a future of confidence and resilience.