Red Teaming Services by DigiFortex: Proactively Securing Your Business
In today’s digital era, cyber threats are not just a possibility—they are a reality. Businesses of all sizes face risks that can disrupt operations, harm reputations, and compromise sensitive data. At DigiFortex, we go beyond traditional cybersecurity to offer Red Teaming Services—a proactive and strategic approach to testing your defences against real-world cyberattacks.
We don’t just uncover vulnerabilities; we help you strengthen your security posture and build confidence in your digital resilience.
Request free consultation - Click Here
.png)
What is Red Teaming?
Red teaming goes beyond traditional penetration testing. It is a strategic simulation of real-world cyberattacks, where ethical hackers act as adversaries to uncover vulnerabilities in your organization’s systems, networks, and processes. By thinking like malicious attackers, red teams can identify not just technological flaws, but also weaknesses in human behaviour and operational workflows.
This isn’t just about finding holes—it’s about revealing the pathways attackers could exploit to reach critical assets, compromise data, or disrupt operations.
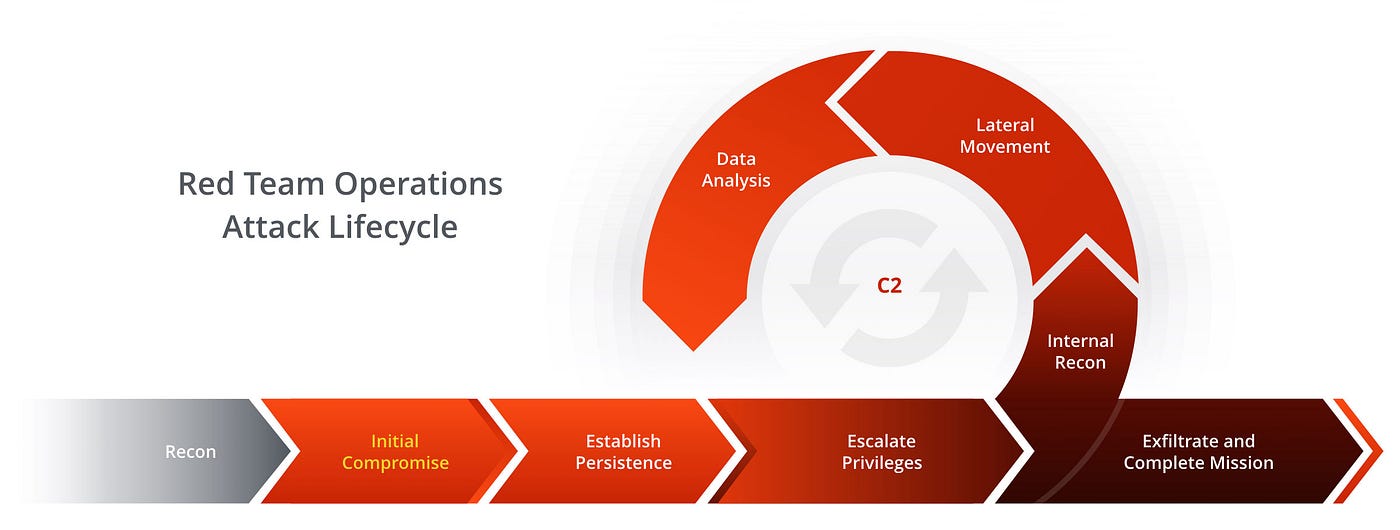
The Red Teaming Process: How Does It Work?
Red teaming engagements are conducted with precision and intent. Here’s how it unfolds:
-
Reconnaissance:
The process begins with gathering intelligence about the organization. From analysing publicly available data to leveraging advanced tools for network mapping, red teams build a blueprint of their target. -
Exploitation:
Once reconnaissance is complete, the team looks for exploitable vulnerabilities. This could involve phishing campaigns, exploiting unpatched systems, or taking advantage of weak user credentials. -
Privilege Escalation:
The goal isn’t just to gain access—it’s to gain control. By escalating privileges, attackers aim to obtain higher levels of access to sensitive systems or data. -
Lateral Movement:
Skilled attackers know how to move undetected within a network, hopping between systems and uncovering additional vulnerabilities. Red teams simulate this process to reveal hidden risks. -
Execution of Objectives:
The attack culminates in achieving specific goals, such as data exfiltration or system compromise, providing a realistic measure of your organization’s security posture. -
Reporting and Debriefing:
A comprehensive report details vulnerabilities discovered, attack paths used, and prioritized recommendations for remediation.
Tools and Techniques in Red Teaming Engagements
At DigiFortex, we use a mix of cutting-edge tools and advanced techniques to deliver realistic and effective red teaming engagements.
-
Reconnaissance Tools:
- Nmap: For scanning and mapping networks to identify open ports and vulnerabilities.
- Maltego: To gather and analyse open-source intelligence (OSINT).
- theHarvester: For gathering emails, domains, and IPs from public sources.
-
Exploitation Tools:
- Metasploit Framework: A widely used platform for discovering and exploiting vulnerabilities.
- Burp Suite: For testing web application security.
- Cobalt Strike: A powerful tool for simulating advanced persistent threats (APTs).
-
Privilege Escalation Techniques:
- PowerSploit: For post-exploitation activities like privilege escalation.
- Mimikatz: To extract credentials and escalate access.
-
Lateral Movement Tools:
- BloodHound: For mapping relationships in Active Directory to find paths for lateral movement.
- PsExec: To execute commands on remote systems.
- CrackMapExec: For testing credential reuse and lateral movement.
-
Custom Malware and Payloads:
- Customized Scripts: Designed to bypass security solutions like antivirus and EDR systems.
- Phishing Kits: To simulate email-based social engineering attacks.
-
Advanced Techniques:
- Social Engineering: Using human psychology to trick employees into granting access.
- Living Off the Land (LotL): Exploiting built-in tools like PowerShell to avoid detection.
These tools and techniques enable us to simulate the tactics of modern threat actors, providing you with a realistic test of your security defences.
Request free consultation - Click Here
Red Teaming vs. Traditional Security Testing
Unlike regular penetration testing, which focuses on specific systems or applications, red teaming evaluates your entire organization’s ability to prevent, detect, and respond to attacks.
It’s about understanding your security from the attacker’s perspective and ensuring you’re ready for even the most sophisticated threats.
Red Teams, Blue Teams, and Purple Teams: Building Collaborative Security
In cybersecurity, collaboration is key:
- Red Teams simulate attacks to test your defences.
- Blue Teams are your defenders, monitoring and protecting your systems.
- Purple Teams combine the strengths of both, ensuring lessons from red teaming improve blue team strategies.
At DigiFortex, we help you integrate these roles into a seamless and effective security strategy.
Challenges in Red Teaming
Red teaming offers invaluable insights into cybersecurity but comes with several challenges. Here’s how DigiFortex tackles them:
-
Balancing Realism and Safety:
Simulating attacks without disrupting operations is complex. DigiFortex ensures controlled testing to maintain system integrity. -
Bypassing Advanced Defenses:
Modern tools like EDR and firewalls are hard to evade. We use stealth techniques and cutting-edge tools to mimic sophisticated attackers. -
Complex IT Environments:
Navigating hybrid and legacy systems is challenging. Our experts adapt strategies for diverse infrastructures. -
Evolving Threats:
Keeping up with rapidly changing attack methods is essential. DigiFortex continuously updates tools and methodologies to stay ahead. -
Avoiding Early Detection:
Premature detection limits effectiveness. Our team employs covert tactics to simulate real-world attackers. -
Human Element Risks:
Social engineering tests can be sensitive. We conduct ethical tests and train employees to enhance awareness. -
Resource and Time Constraints:
Extensive testing requires time and resources. DigiFortex prioritizes high-risk areas for efficient and impactful results. -
Actionable Insights:
Translating findings into actionable plans is critical. We provide clear, tailored reports for both technical teams and executives.
DigiFortex turns these challenges into opportunities, ensuring your organization is prepared for the most sophisticated threats. Partner with us to secure your digital future.
Why Choose DigiFortex for Red Teaming?
At DigiFortex, we pride ourselves on delivering cybersecurity solutions that are trusted, effective, and tailored to your needs. Here’s why businesses choose us:
- Certified Experts: CIPPE, CCSA, CCNA, HPOV, DCPLA, CEH, CISSP, CISM, ISO27001:2022.
-
Proven Credentials:
DigiFortex is ISO 27001:2022 certified and CERT-In Empanelled for providing Information Security Auditing Services, we adhere to the highest standards in the industry. -
Customized Solutions:
Every business is unique, and so are its challenges. We design our red teaming engagements to align with your specific goals and industry requirements. -
End-to-End Support:
From identifying risks to implementing improvements, we’re with you every step of the way.
Partner with DigiFortex to Secure Your Business
At DigiFortex, we believe cybersecurity is more than just protection—it’s about building trust, ensuring continuity, and enabling growth. Our Red Teaming Services are designed to help your business thrive in an increasingly complex digital landscape.
By choosing DigiFortex, you’re not just getting a service provider—you’re gaining a trusted partner committed to safeguarding your success.
Let’s Build a Stronger Future Together
Your security is our mission. Contact Digifortex today! to learn how our Red Teaming Services can help you stay ahead of cyber threats and build a future of confidence and resilience.
