DigiFortex: Your Trusted Partner in Network Penetration Testing
In today's digital age, cyber threats are constantly evolving, targeting businesses of all sizes. At DigiFortex, we understand the critical importance of protecting your network, data, and systems. That’s why we specialize in Network Penetration Testing—a proactive way to uncover vulnerabilities in your network before hackers can exploit them.
What is Network Penetration Testing?
Network Penetration Testing, also known as Network Security Testing, is a simulated cyberattack on your network infrastructure aimed at identifying security weaknesses. The process involves assessing your network architecture, devices, servers, firewalls, and other components to find vulnerabilities that a hacker could exploit to gain unauthorized access, steal sensitive information, or disrupt services.
By performing Network Penetration Testing, we can uncover issues such as open ports, misconfigured firewalls, unpatched software, and weak access controls. Once vulnerabilities are identified, we provide actionable recommendations for improving your network's security posture.
Request free consultation - Click Here
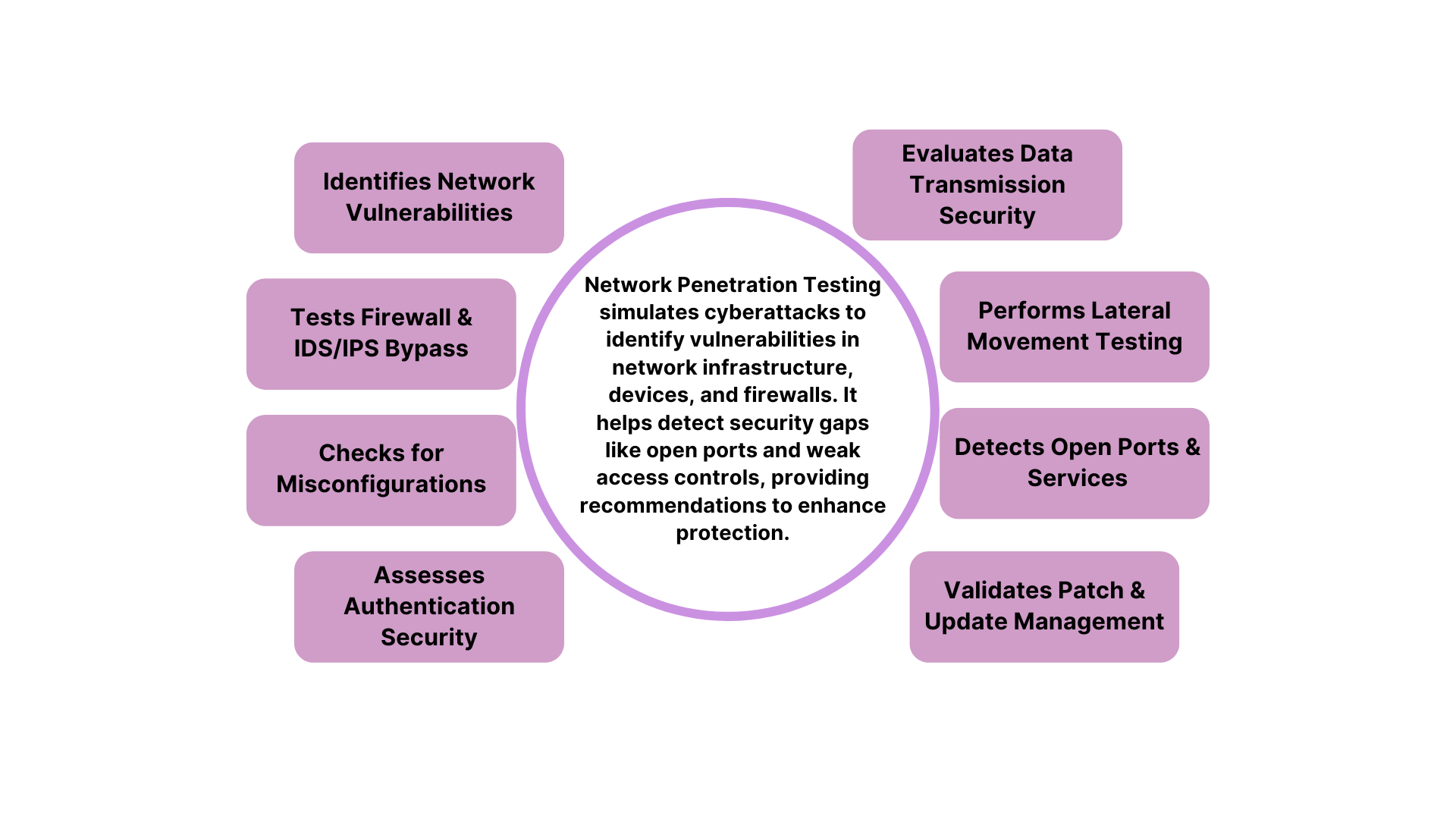
Network Penetration Testing in VAPT Includes:
-
Identifies Network Vulnerabilities:
Finds security flaws in internal and external networks. -
Tests Firewall & IDS/IPS Bypass:
Evaluates firewall rules and intrusion detection system effectiveness. -
Checks for Misconfigurations:
Detects weak security settings in routers, switches, and servers. -
Assesses Authentication Security:
Ensures strong access controls and prevents unauthorized logins. -
Evaluates Data Transmission Security:
Tests encryption protocols to protect data in transit. -
Performs Lateral Movement Testing:
Simulates how attackers spread within the network after gaining access. -
Detects Open Ports & Services:
Looks for flaws in multi-factor authentication methods. -
Validates Patch & Update Management:
Checks if critical security updates are applied.
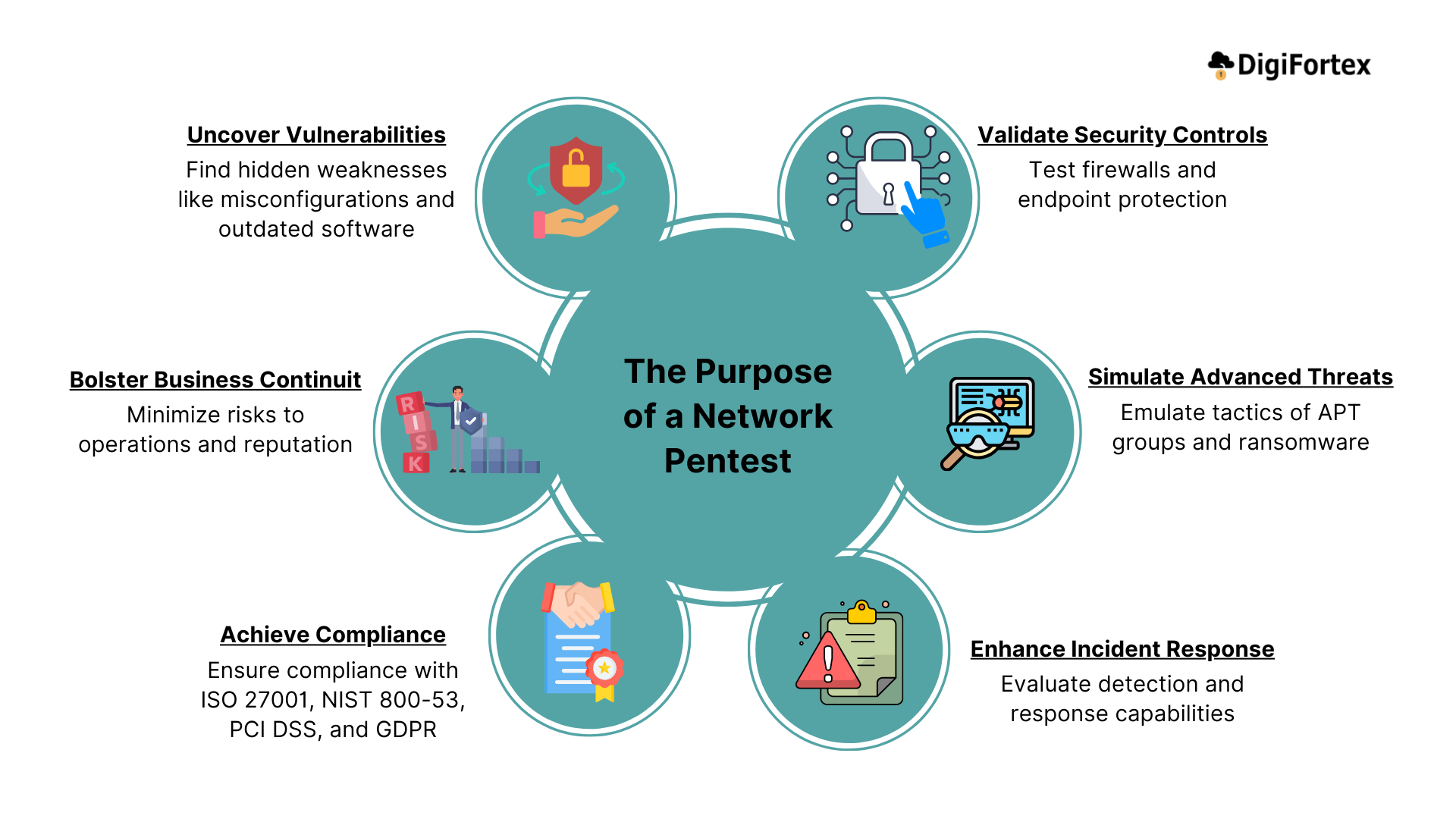
The Purpose of a Network Penetration Test
A network penetration test goes beyond routine vulnerability scans by actively exploiting weaknesses to assess their real-world impact. The purpose is to:
-
Uncover Hidden Vulnerabilities:
Discover misconfigurations, outdated software, and weak security controls that scanners may miss. -
Validate Security Controls:
Test the effectiveness of firewalls, intrusion prevention systems, and endpoint protection solutions. -
Simulate Advanced Threats:
Emulate the tactics used by threat actors, including APT groups and ransomware operators. -
Enhance Incident Response:
Gauge how well the organization detects and responds to attacks. -
Achieve Compliance:
Fulfil requirements for frameworks like ISO 27001, NIST 800-53, SOC 2, PCI DSS, and GDPR. -
Bolster Business Continuity:
Minimize the risk of downtime, data breaches, and reputational damage.
Common Vulnerabilities in Network Security
Network Penetration Testing helps identify many common vulnerabilities that could put your business at risk. Some of the most prevalent vulnerabilities we look for include:
-
Unpatched Software:
Software and firmware on network devices can become vulnerable over time if not updated regularly. -
Weak Authentication:
Weak passwords and lack of multi-factor authentication allow attackers to easily compromise user accounts and access sensitive data. -
Unsecured Ports and Services:
Open ports and unsecured network services provide attackers with easy entry points into your network. -
Misconfigured Network Devices:
Routers, firewalls, and other network devices often have misconfigurations that can lead to unauthorized access. -
Insecure Protocols:
Fulfil requirements for frameworks like ISO 27001, NIST 800-53, SOC 2, PCI DSS, and GDPR. -
Lack of Network Segmentation:
Without proper segmentation, attackers who gain access to one part of the network can easily move laterally to access other critical systems.
Request free consultation - Click Here
DigiFortex Network Penetration Testing Approach
At DigiFortex, we take a comprehensive approach to Network Penetration Testing, leveraging the latest tools, methodologies, and industry best practices to identify and mitigate risks. Our team of certified security experts follows a structured process to test your network’s security effectively.
-
Reconnaissance and Information Gathering
The first step in our penetration testing process is to gather as much information as possible about your network. This involves both passive and active techniques, including:
- Network Scanning: Identifying the devices connected to your network, including routers, servers, workstations, and firewalls.
- OS Fingerprinting: Determining the operating systems running on your devices to identify potential vulnerabilities specific to those platforms.
- DNS Interrogation: Gathering DNS records to understand your network structure and identify potential targets.
- Social Engineering: In some cases, we use controlled social engineering techniques to test your employees’ susceptibility to phishing and other tactics used by attackers to gain access to your network.
-
Vulnerability Scanning
Once we’ve gathered enough information, we use automated tools and manual techniques to identify vulnerabilities in your network’s infrastructure. Common vulnerabilities include:
- Open Ports: Unnecessary open ports can provide attackers with an entry point to your network.
- Weak Passwords: Easily guessable passwords or lack of multi-factor authentication (MFA) can leave accounts exposed.
- Outdated Software: Unpatched systems and outdated software are prime targets for attackers exploiting known vulnerabilities.
- Misconfigured Firewalls: Incorrectly configured firewalls can allow unauthorized access to your network.
- Unsecured Protocols: Using outdated or insecure communication protocols like FTP or Telnet increases the risk of unauthorized access.
-
Exploitation and Attack Simulation
After identifying vulnerabilities, our next step is to simulate an attack on your network. This is the critical phase where we attempt to exploit vulnerabilities and gain unauthorized access to your network. Some of the techniques we use include:
- Exploiting Open Ports: We test open ports for weaknesses and attempt to gain access to devices or services running on them.
- Password Cracking: Using tools like brute-force attacks or dictionary attacks, we attempt to crack weak passwords and gain access to sensitive systems.
- Privilege Escalation: If we gain access to one part of the network, we attempt to escalate privileges to gain control over critical systems.
- Denial-of-Service (DoS): We simulate DoS attacks to assess whether your network can withstand traffic spikes or other attacks designed to overwhelm network resources.
-
Post-Exploitation and Lateral Movement
After gaining access to your network, we simulate the behavior of an attacker attempting to move laterally within your network. This helps us identify potential paths an attacker might take to access additional systems, data, or credentials. Key activities during this phase include:
- Accessing Sensitive Data: We test the network’s ability to protect sensitive data and determine if attackers can move laterally to access confidential business information.
- Privilege Escalation: We attempt to elevate our access level to gain control over higher-value systems and servers.
- Persistence: We assess how an attacker could maintain access to your network over time, even if they were detected initially.
-
Reporting and Remediation
After completing the penetration testing process, we provide you with a detailed report outlining all identified vulnerabilities, how we exploited them, and the risks associated with each issue. The report includes:
- Vulnerability Summary: A description of each vulnerability discovered, including its severity and potential impact.
- Attack Scenarios: Detailed scenarios of how the vulnerabilities were exploited and the data or systems compromised.
- Recommendations: Actionable steps to remediate each vulnerability and improve your network security, such as updating software, strengthening authentication processes, or reconfiguring firewalls
- Remediation Recommendations
Request free consultation - Click Here
Best Practices for Network Penetration Testing
To ensure your network is as secure as possible, we recommend the following best practices:
-
Perform Regular Testing:
Network Penetration Testing should be done regularly to identify new vulnerabilities that could arise due to changes in your network or the introduction of new devices. -
Update Software and Hardware:
Regularly patch software and firmware to ensure that known vulnerabilities are addressed. Ensure that your devices are up to date with the latest security patches. -
Use Strong Authentication:
Implement strong password policies and use multi-factor authentication (MFA) wherever possible to secure access to critical systems. -
Segment Your Network:
Proper network segmentation helps limit the spread of attacks and protects sensitive data from being accessed by unauthorized users. -
Educate Employees:
Train employees on network security best practices, including how to spot phishing attempts and secure their devices.
Advanced Trends in Network Penetration Testing
-
Zero Trust Penetration Testing:
Ensuring robust implementation of Zero Trust Architecture (ZTA) by testing segmentation, least privilege policies, and access controls. -
AI-Augmented Pentesting:
Using AI-driven tools to uncover hidden vulnerabilities and predict attack vectors more effectively. -
Pentesting as a Service (PTaaS):
Continuous, subscription-based testing to maintain security in real-time. -
Focus on Cloud and Hybrid Networks:
Testing cloud-native applications and hybrid infrastructures, especially in AWS, Azure, and GCP environments. -
IoT and OT Security Assessments:
Evaluating the security of Internet of Things (IoT) devices and operational technology (OT) systems, which are prime targets for cyberattacks. -
Red Teaming Exercises:
Combining network pentesting with full-scale attack simulations to test organizational resilience comprehensively.
Best Practices for Effective Web Application Penetration Testing
-
Use OWASP Top 10 as a Baseline
Focus on the vulnerabilities listed in the OWASP Top 10, which include the most critical web application risks. -
Incorporate DevSecOps Practices
Integrate security testing into the development lifecycle to identify and fix vulnerabilities early. -
Leverage Modern Penetration Testing Tools
Use advanced tools and platforms that offer automated scanning, AI-driven analysis, and cloud-specific testing. -
Conduct Regular Testing
Perform Penetration Testing periodically, especially after major updates or new feature releases. -
Engage Certified Experts
Hire professionals with certifications like CEH, CISSP, or OSCP for thorough and reliable testing. -
6. Document Everything
Keep detailed records of vulnerabilities, remediation efforts, and testing methodologies for future reference.
Request free consultation - Click Here
How DigiFortex Leads in Network Penetration Testing
As a CERT-In empanelled and ISO 27001:2022-certified organization, DigiFortex offers industry-leading penetration testing services tailored to address the unique needs of modern enterprises.
Why Partner with DigiFortex?
-
Certified Experts
CIPPE, CCSA, CCNA, HPOV, DCPLA, CEH, CISSP, CISM, ISO27001 LA, -
ISO 27001:2022 certified and CERT-In empanelled:
DigiFortex is ISO 27001:2022 certified and CERT-In empanelled for providing Information security services. We bring unparalleled expertise to every project. -
Regulatory Expertise:
In-depth knowledge of compliance frameworks to ensure your organization meets regulatory requirements. -
Actionable Insights:
Detailed reports with clear recommendations for both technical and executive audiences.
Let’s Secure Your Network Together
Take the first step toward stronger cybersecurity. Partner with DigiFortex for Network Penetration Testing and experience the confidence that comes from being one step ahead of attackers.
Contact us today to schedule your assessment!
Request free consultation - Click Here
Let’s Build a Stronger Future Together
Your security is our mission. Contact Digifortex today! to learn how our Network Penetration Testing Services can help you stay ahead of cyber threats and build a future of confidence and resilience.