API VAPT by DigiFortex
API Penetration Testing: Protect Your Business from Cyber Threats with DigiFortex
In today’s interconnected world, APIs (Application Programming Interfaces) are at the heart of most online services. They enable smooth communication between applications, but they also introduce vulnerabilities that hackers can exploit. At DigiFortex, we specialize in API penetration testing to help businesses like yours protect their digital assets from potential security threats.
What is API Penetration Testing ?
API stands for Application Programming Interface. It’s like a messenger that allows different software programs to communicate with each other. APIs allow one program to request data or services from another, without needing to understand how the other program works internally. For example, when you use an app to check the weather, the app might use an API to get weather data from a server.
API Penetration Testing is the process of testing these APIs for security vulnerabilities. Just like how hackers try to break into systems, penetration testers try to find weaknesses in the APIs to make sure they are safe from attacks. The goal is to ensure that the API doesn't expose sensitive data or allow unauthorized actions by malicious users.
By simulating attacks on your API, DigiFortex helps you find and fix these security flaws before attackers do, ensuring your data and systems remain safe.
Request free consultation - Click Here
Why is API Penetration Testing Important?
APIs are everywhere — from mobile apps and web services to IoT devices and cloud platforms. They handle critical data exchanges, making them a prime target for hackers. A single vulnerability in an API can lead to devastating breaches, exposing sensitive customer data and compromising business integrity. By performing regular API penetration testing, businesses can:
-
Identify Security Gaps:
Find vulnerabilities like SQL injection, broken authentication, data exposure, and improper permissions. -
Protect Customer Data:
Ensure sensitive information such as login credentials, financial details, and personal data are securely transmitted. -
Meet Compliance Standards:
Adhere to security frameworks and regulations like GDPR, HIPAA, and ISO 27001 to avoid penalties.
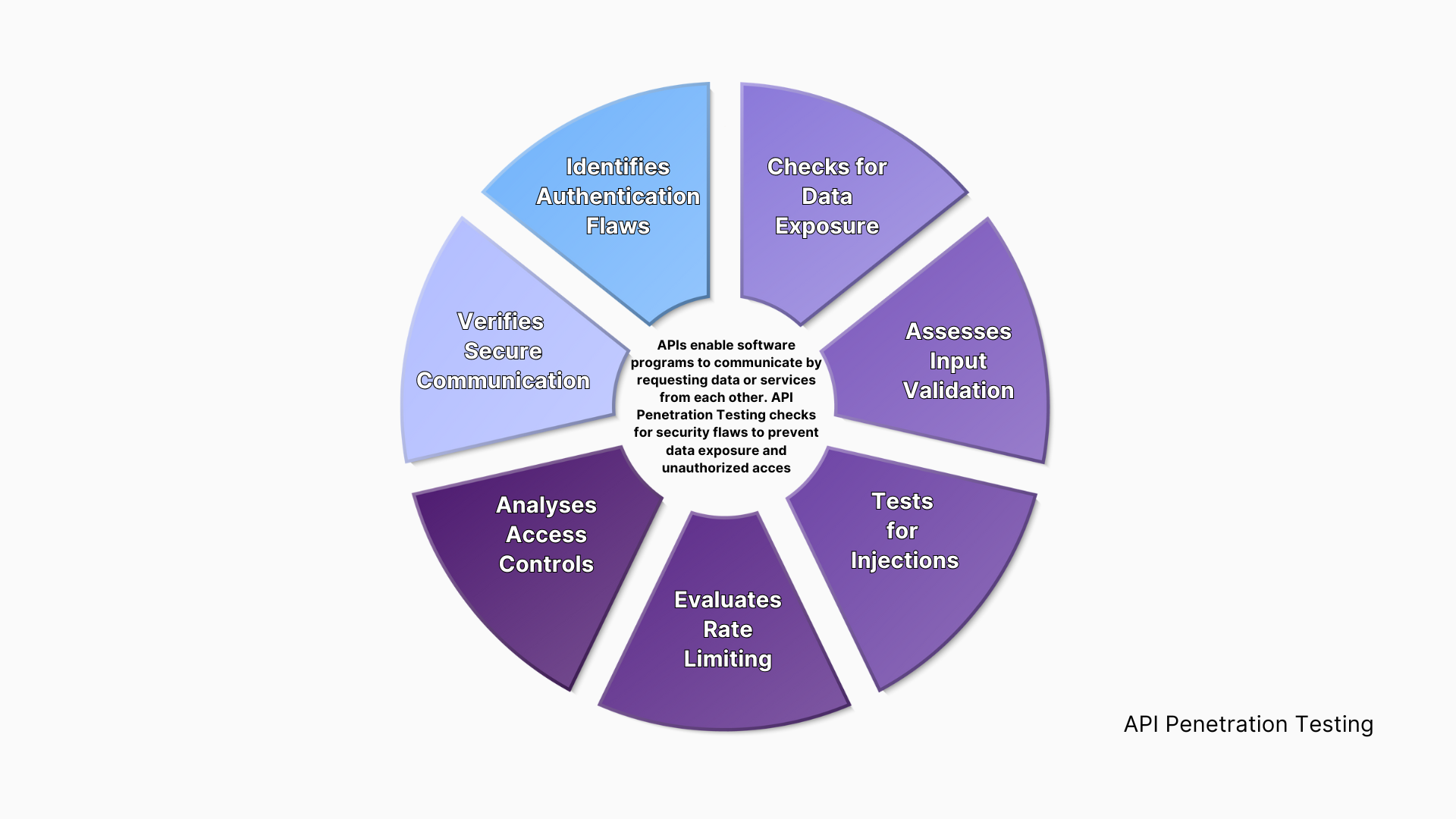
API Penetration Testing Includes:
-
Identifies Authentication Flaws:
Tests for weaknesses in API authentication mechanisms. -
Checks for Data Exposure:
Ensures sensitive data is not unintentionally exposed via APIs. -
Assesses Input Validation:
Verifies that APIs properly validate and sanitize user inputs to prevent attacks. -
Tests for Injections:
Detects injection flaws such as SQL injection or XML injection within API endpoints. -
Evaluates Rate Limiting:
Checks for protections against denial-of-service (DoS) attacks. -
Analyses Access Controls:
Ensures proper authorization checks are in place for different user roles. -
Verifies Secure Communication:
Ensures APIs use secure protocols like HTTPS to protect data in transit.
Modern Techniques in API Penetration Testing
With the evolution of technology, new techniques in API penetration testing have emerged:
-
GraphQL Testing:
APIs using GraphQL are gaining popularity due to their flexible query capabilities. However, they can be complex and difficult to secure. Testing for GraphQL-specific vulnerabilities is essential to avoid issues like excessive data exposure. -
OAuth and OpenID Testing:
OAuth is commonly used for authorization, and OpenID is used for authentication. Testing these protocols for flaws in token handling or authorization logic is crucial to prevent unauthorized access. -
Automated API Security Tools:
Tools like Burp Suite, Postman, and OWASP ZAP help automate the process of testing APIs for vulnerabilities. These tools can scan for known issues and speed up the overall testing process. -
JWT Token Testing:
Many APIs use JSON Web Tokens (JWT) for secure data exchange. However, flaws in token implementation, such as weak signing algorithms, can expose the API to security risks. Properly testing JWT tokens is vital. -
API Rate Limiting Testing:
Modern APIs require strict rate limiting to prevent abuse. Testing how an API handles rate limits and ensuring there are no vulnerabilities that can be exploited is a key part of testing.
Request free consultation - Click Here
DigiFortex API Penetration Testing Process:
-
Planning and Scope Definition
The first step in API penetration testing is defining the scope of the test. This phase involves collaboration between the penetration testing team and the client to understand the following:
- API Endpoints: Identifying all API endpoints and their functionalities.
- Authentication and Authorization: Assessing how users authenticate and what permissions they have (e.g., OAuth, API keys, JWT).
- Sensitive Data Handling: Determining what sensitive data, the API handles and how it is protected (e.g., encryption, TLS).
- Security Protocols: Reviewing the security protocols used, such as HTTPS or SSL/TLS.
This phase is vital for ensuring the test focuses on critical areas and aligns with your business needs.
-
Information Gathering
Once the scope is defined, the next step is to gather information about the API. This includes:
- API Documentation: Reviewing the API documentation to understand its structure, authentication methods, and data flow.
- Network Traffic Analysis: Capturing network traffic between the client and server to identify sensitive data exchange and endpoints.
In this phase, the penetration testers begin to identify potential attack vectors and build a map of the API’s attack surface.
-
Automated Vulnerability Scanning
Automated scanning tools are used to detect common vulnerabilities in APIs. These tools test for issues such as:
- Injection Flaws: SQL injection, XML injection, or other injection attacks that can compromise the API's data.
- Broken Authentication: Identifying flaws in login mechanisms, such as default credentials or inadequate password strength.
- Sensitive Data Exposure: Checking if sensitive data, like passwords or personal information, is improperly exposed during transmission.
- Cross-Site Scripting (XSS): Testing for malicious code injections into the API’s data or responses.
Automated tools help speed up the process by quickly identifying basic, known vulnerabilities across all tested endpoints.
-
Manual Penetration Testing
While automated tools can identify some common flaws, manual penetration testing is necessary to detect more complex vulnerabilities. In this phase, testers simulate real-world attacks, such as:
- Bypassing Authentication: Attempting to bypass authentication mechanisms like API keys or OAuth tokens to gain unauthorized access.
- Logic Flaws: Testing for logic vulnerabilities, such as account takeover, data manipulation, or privilege escalation, which can only be detected through human analysis.
- Session Management: Analysing session handling and token management to ensure they are securely implemented and expire as needed.
Manual testing is crucial for identifying vulnerabilities that automated tools might miss, such as flaws in business logic or complex authorization mechanisms.
-
Access Control Testing
One of the most important aspects of API Penetration Testing is ensuring that the access control mechanisms are robust. This step involves testing:
- Role-Based Access Control (RBAC): Verifying that users only have access to resources according to their roles and permissions.
- Privilege Escalation: Attempting to exploit flaws in the authorization process to escalate user privileges.
- Token Validation: Ensuring that tokens (such as JWT) are securely validated and cannot be tampered with to gain unauthorized access.
This phase helps confirm that users cannot access resources they are not authorized to interact with.
-
Business Logic Testing
APIs often execute complex business logic that can be vulnerable to attacks. This step involves testing for scenarios like:
- Account Takeover: Manipulating requests to change user credentials or hijack accounts.
- Transaction Manipulation: Altering financial or transactional data to carry out unauthorized actions.
- Data Integrity: Ensuring that data cannot be modified or deleted without proper authorization
Testing business logic helps prevent exploits that go beyond simple technical flaws, focusing on how APIs handle data and transactions.
-
Reporting and Recommendations
After the testing is completed, the penetration testers provide a comprehensive report that includes:
- Vulnerabilities Detected: A list of all identified vulnerabilities, including their severity.
- Exploitability: Explanation of how each vulnerability could be exploited by attackers.
- Fix Recommendations: Actionable recommendations for mitigating each vulnerability, such as fixing authentication mechanisms, strengthening encryption, or updating outdated libraries.
This report is essential for informing your development team about where improvements are needed and guiding remediation efforts.
-
Post-Testing Support and Retesting
Once vulnerabilities are fixed, it's important to ensure that the changes are effective. DigiFortex provides post-testing support, which includes:
- Retesting: Reassessing the API to verify that all identified vulnerabilities have been successfully patched.
- Ongoing Monitoring: Helping set up continuous monitoring of API traffic to detect potential future threats.
- Security Training: Educating your development team on secure coding practices to prevent the introduction of vulnerabilities in future iterations of the API.
Request free consultation - Click Here
Best Practices for Advanced API Security
To build and maintain secure APIs, follow these best practices:
-
Strong Authentication and Token Management:
Use strong token validation methods, rotate keys regularly, and ensure that JWTs have appropriate expiration times. -
Encryption at Rest and in Transit:
Always encrypt sensitive data both during transmission (using HTTPS) and when stored on servers or databases (using encryption standards like AES-256). -
Implement Rate Limiting and IP Blacklisting:
Protect your APIs from brute-force attacks and DoS by applying rate limiting and setting up IP blacklisting mechanisms. -
Code Review and Dependency Scanning:
Regularly review API code and scan dependencies for known vulnerabilities using automated tools. -
Keep APIs Updated:
As new vulnerabilities are discovered, it’s critical to apply patches and security updates promptly. Keeping up with the latest security standards helps minimize risks.
Secure Your Business with DigiFortex
At DigiFortex, we are committed to helping you build a secure digital infrastructure. Our API penetration testing services are designed to identify risks and strengthen your defences, enabling your business to thrive in a secure environment.
Don’t wait for a breach to occur. Protect your API, safeguard your data, and ensure your business continuity with DigiFortex — your trusted partner in cybersecurity.
Contact DigiFortex today to learn more about how our expert API penetration testing services can help secure your APIs against the latest threats. Stay ahead, stay secure.
Request free consultation - Click Here
Let’s Build a Stronger Future Together
Your security is our mission. Contact Digifortex today! to learn how our API Penetration Testing Services can help you stay ahead of cyber threats and build a future of confidence and resilience.